Microsoft Windows comes in many variants with barely visible feature differences. A noticeable variation is observed when we have to choose between a 32-bit or a 64-bit version. Lack of knowledge regarding the basic difference between a 32-bit and a 64-bit operation system adds to the puzzlement when it comes to deciding the appropriate version.
Microsoft started releasing 64-bit versions shortly after the launch of their well-liked and fantasized Windows XP, which had the longest product lifespan of around 14 years. Time-traveling into the history reveals that the very first implementation of the 64-bit operating system was a Unix-like UNICOS created by the supercomputer-maker Cray Inc. in 1985. The development continued and many operating systems — Mac OS X, Windows, Solaris, and the most recently Google’s Android — were baked into their 64-bit versions.
A ‘bit’ of knowledge
What does a bit stand for? The smallest piece of data in a computer is known as a bit or binary digit. We know that computer only understands binary language (the 0s and 1s), so, each and every bit can have only one binary value, either 0 or 1. A computer stores data in a collection of such bits known as a byte. 8 bits make up a byte, also called an octet.
Something about the 32-bit vs 64-bit processors
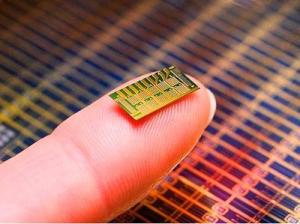
A processor or CPU includes a number of registers and logical circuits. Also called the brain of the computer, people often confuse CPU with the cabinet of a desktop computer. The size of the register is 32-bit in a 32-bit CPU and similar for 64-bit. The number of values that can be stored in its register are 2^32. These values are used to map the address of the memory locations present in the physical memory. So, 2^32 = 4 gigabytes is the amount of memory or RAM a 32-bit processor can access during its operation.
In the case of 64-bit, the register can store 2^64 values that amount to 16EB (exabytes) of RAM. A grand figure when to compared to 4 GB memory that could be accessed by its 32-bit older counterpart.
A 32-bit CPU can process 4 bytes of data in one CPU cycle as 8 bits are equal to 1 byte. So, if the size of the data to be processed is greater than 4 bytes, it would require the CPU to go for another cycle to process the remaining data. In the case of a 64-bit CPU, the whole data, if less than 8 bytes, could be processed in a single go. Even if the data is more than 8 bytes, the 64-bit processor would require less time than the other one. You’ll not be able to notice much difference in normal day usage, except that you are the one who likes to multi-task between heavy applications. A 64-bit processor comes in multi-core options enabling more processing power without increasing the size of the hardware.